Track 1
Are We Too Early for the Party?: The Perils of Early Cyber Engineering
Presented by Lillian Baker, Product Security Engineer & Steve Bichler, Senior Cybersecurity Test Engineer
The authors had the rare opportunity bringing into the building of a cybersecurity solution at the very beginning of a program. This is a rundown of their experiences, and both the difficulties and positive aspects of building security in from the beginning of a program. The speakers will outline the issues such as: 1) How to build security requirements when there are no system requirements; 2) Threat Modeling a system that does not exist; 3) Project Management Issues: evolving timelines, lack of processes, and changing organizational dynamics; 4) dealing with partners/suppliers; 5) Planning for items in the architecture that won’t be ready for years. Additionally, they will talk through the benefits: 1) Adding requirements early, 2) Having a marker in place, 3) Compliance defined early. Finally, they will provide their recommendations on how best to handle being brought in early
Gone Vishing: A DEFCON31 Social Engineering Story
Presented by Jeff Tomkiewicz, Penetration Tester
Beyond PayPal and Venmo - What is Money in the Digital Era?
Presented by Adrian Cercenia
Geolocation Tracking Using Open-Source Mapping Databases
Presented by Anna Quinn, Penetration Tester and Security researcher
Through use of online Open-Source Databases, it has become alarmingly easy to discover the precise geographical location of a photo. After being inspired by others in the field, I have performed research on using OpenStreetMaps to associate a photo with its proper location. In this talk I will walk attendees through usage of Overpass-Turbo and guide them through the methodology required to discover identifying features in a photo which might disclose its location. I have multiple examples listed in this talk as well as a live demo towards the end, allowing for exposure to differing methods and techniques. These techniques could help in investigations across multiple disciplines within cybersecurity, whether it is for determining whether an atypical travel alert might be benign, finding information on a phishing target, or even aiding in missing persons investigations.
Teaching Information Warfare: Strategies in Academic and Government Institutions
Presented by Dr. Gregory Carpenter, CSO at KnowledgeBridge Internaional
This presentation provides a concise overview of the teaching strategies employed in academic and government institutions to educate individuals on information warfare. Academic institutions integrate these disciplines into their curricula, while government institutions, and academies, also emphasize specialized training programs. The multidisciplinary nature of information warfare actively encompasses cybersecurity, psychological operations, Operations Security, electronic warfare, deception techniques, and associated intelligence support. Curriculum integration involves adapting existing programs to address emerging information warfare threats. Specialized training initiatives, such as workshops and simulations, enhance preparedness and response capabilities in government institutions. This presentation emphasizes the role of academic and government institutions in equipping individuals with the knowledge and skills required to navigate the complexities of information warfare. To highlight the foundational differences in approach, we investigate similarities and differences in policy and lexicons unique to distinct cultures. By adopting interdisciplinary approaches, adapting curricula, providing specialized training, and considering cultural nuances, these institutions contribute to developing competent professionals capable of safeguarding national security in the digital age.
Workshops & CTFs
Dive into Purple Teaming: Master the Art of Collaborative Cyber Ops
Presented by CyberNEX
Join our immersive workshop and gain comprehensive insights into collaborative cybersecurity practices. Through interactive exercises, you'll delve into the intricacies of planning, executing, and retrospecting security scenarios from both offensive (Red Team) and defensive (Blue Team) standpoints. Harness the power of CYYNC Community Edition, a cutting-edge collaborative platform for cyber teams. By bridging the gap between Red and Blue Teams, you'll enhance your ability to anticipate, counteract, and mitigate evolving cyber threats effectively. Elevate your skills in a dynamic, collaborative environment and emerge better equipped to safeguard your digital assets. Don't miss this opportunity to propel your cybersecurity expertise to new heights.
*Participants are expected to bring a laptop
Hack Our Drone
Presented by Ronald Broberg, Dark Wolf Solutions
The Hack Our Drone Workshop provides participants with the opportunity to work through 'hands-on' lab modules focused on the components of an Unmanned Aerial System including the Vehicle (UAV), Ground Control System (GCS), and communication subsystem. Participants are expected to bring a laptop either with Kali Linux installed or bootable to a Kali Linux USB Thumb drive. All other equipment is provided.
Unmanned Aerial Systems – Platform Security CTF
Presented by CT Cubed
Discover the exciting world of cybersecurity and unmanned aerial systems (UAS)! Learn how to safeguard UAS from all angles with a comprehensive platform security perspective. Engage in some fun and challenging CTF adventures where you can put your skills to the test. See firsthand how your actions affect our UAS demonstrator. The UAS demonstrator contains all the sensors from our Mobile Optical Ultrasonic Sensor Explorer, or MOUSE for short. The MOUSE represents a small Unmanned Aircraft System (sUAS) comprising a pan/tilt object recognition camera, navigation camera, temperature & humidity sensor, ultrasonic sensor, and drive system powering four motors. You won't need to worry about any complicated registration process; all you need is your personal laptop to join in the excitement. Earn enough points in the challenge, and you could be the proud owner of a CT Cubed SAO, a special prize while supplies last. Get ready to embark on this fascinating journey and prove your cybersecurity prowess!
Wireless Capture the Flag (CTF)
Presented by Ronald Broberg, Dark Wolf Solutions
Wireless Capture the Flag offers both WiFi 802.11 challenges and other radio frequency challenges across the spectrum. Bring your own gear or borrow some of ours. Introductory walk-throughs will be offered to those who just want to come and learn.
BSides Colorado Springs CTF
Presented by Hackers N' Hops
A beginner to intermediate difficulty, jeaparody style CTF featuring a variety of challenge categories including OSINT, Crypto, and Root the Box.
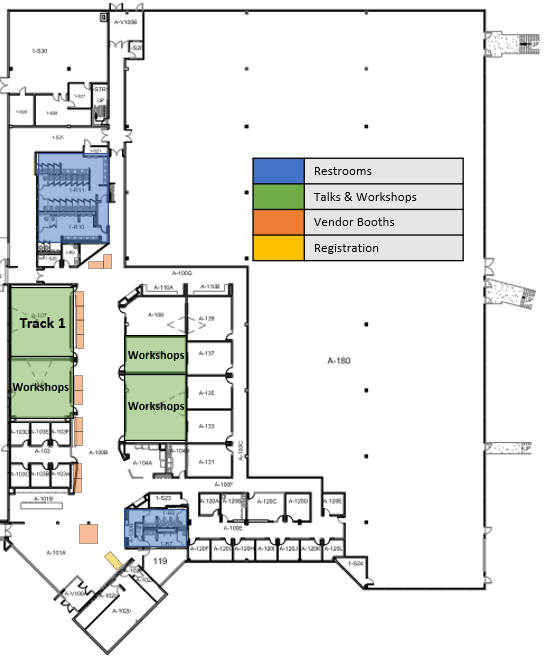
Day 2: Venue Map
Disclaimer: The conference schedule is subject to change without notice due to unforeseen circumstances. Attendees are advised to regularly check for updates on the official conference platform. We apologize for any inconvenience this may cause.