Track 1
From Chaos to Continuous Delivery: Securing your DevOps Pipeline from Hackers, bugs and Co-Workers
Presented by Ben Struebing, Founder & CEO at CyberNEX
Looking for ways to protect your DevOps pipeline from hackers, bugs, and co-workers? We'll cover the foundational concepts of CI/CD, its purpose, and why it's critical for faster time-to-market, improved code quality, and increased collaboration. Learn about the risks and attack vectors for DevOps and gain valuable insights from real-life case studies. Our experts will provide you with the best practices and security tools to maximize the benefits of CI/CD while ensuring a safe pipeline. Don't miss this opportunity to learn key knowledge and strategies for achieving uninterrupted, secure, and efficient continuous delivery!
Defensive Cyber Tool on Kubernetes
Presented by Jon Andrew, Platform Engineer at Defense Unicorns
Kubernetes is an increasingly-popular way of deploying enterprise apps. In addition to being an attractive attack vector for red teams, the benefits that Kubernetes provides might also make it a good platform for blue team deployments for teams willing to endure the steep learning curve. This session looks at some of the benefits and pitfalls awaiting teams that want to try running their tools on top of a Kubernetes cluster.
HiatusRAT: Reading Data Planes and enabling Beacon Layovers
Presented by Daniel Adamitis, Principal Information Security Engineer at Black Lotus Labs
Lumen’s Black Lotus Labs team identified a never-before-seen router campaign targeting business grade routers. This campaign showcased highly advanced adversarial tradecraft, and as we looked beyond our initial discoveries, we began to wonder if we only identified a small component of a larger computer network operations platform that remained untouched for over two years. This presentation will describe a multi-year long Chinese nation-state campaign targeting business grade routers in organizations of strategic importance, focused on intelligence and economic espionage. The primary targets thus far are in the technology, pharmaceutical, government, and energy verticals. The campaign incorporates a capability to passively collect data in transit, and has tooling designed to target all the major architecture of routers. Lastly it consists of a global covert network that allows the threat actor to relay malicious commands and exfiltrate data, by obfuscating their actions in residential IP space circumvent geo-based blocking. We examine the observed aspects of this campaign, and question what else could have been engaged through this platform. At this point we are able unable to correlate this activity to any known public reporting.
The Art of Vishing: How to Pwn a Financial Institution
Presented by JD Seamons, Senior Associate Penetration Tester at Dark Wolf Solutions
Vishing is the practice of eliciting information or attempting to influence action via the telephone and is one of the top four methodologies of malicious social engineering. Come join us as we share a real world story of how we used vishing to infiltrate a financial services institution! During this presentation we will discuss social engineering ethical practices and how to plan and execute a vishing engagement. Additionally, we will highlight some of the tools, techniques and procedures that you can use to conduct your own vishing assessment including phone number spoofing, creating a pretext, and utilizing OSINT. Finally, we will present some of the difficulties we had to overcome during our engagement and share with you sound vishing advice you can bank on!
Navigating the Cybersecurity Terrain with Zarf
Presented by Lauren Mengert, Unicorn Engineer at Defense Unicorns
As a cybersecurity professional, do you find yourself swapping networks and terrain so often that you wish you had a “you are here” map? This requires us to find ways to bring our tools with us and ensure that we are not opening up new attack vectors to the defended environments. Zarf, a fully open-source tool, can help bolster cybersecurity measures in a secure and repeatable fashion. In this session, we will explore how Zarf can deploy software anywhere, including air-gapped, disconnected, or edge environments, while keeping your cybersecurity tools mobile and secure. Furthermore, we’ll discuss how Zarf aids in streamlining DevSecOps capabilities such as Kubernetes clusters management, logging, and Software Bill of Materials (SBOM) compliance, thereby fortifying the security posture. This session won’t just tell you about Zarf’s cybersecurity magic – it will show you using Kali Linux as a real-world example. Witness how Zarf empowers the creation and distribution of cybersecurity tools, ensuring applications stay up and running, no matter how isolated the environment or how often it changes.
Beyond Transparency: Leveraging SBOMs for Maximum Impact
Presented by Mercedes Andreacchi
SBOMs, or Software Bill of Materials, have become a paramount aspect of supply chain risk management. For the sake of compliance, organizations generate this deliverable but tend to overlook the implicit security risk that comes with disclosing the packages and libraries that form the building blocks of their software products. Join us as we explore how SBOMs offer attackers a "peek behind the curtain" and can be leveraged to target and abuse programs in the wild.
The Impact of AI on Cybersecurity: How It Can Improve or Impair Security
Presented by Pradeep Khakural, Zelda Security
AI is revolutionizing the way organizations and cybersecurity providers approach threat detection and response. Automation tools will create improved efficiency and accuracy of the vulnerability management process. Behavior Analytics can help predict anomalies in user behavior and expedite the discovery of compromised accounts. Machine learning can proactively bolster security measures by identifying and predicting potential vulnerabilities before they are exploited. Conversely the same advanced AI tools can embolden threat actors and increase the severity and complexity of cyberthreats. This will create an escalating battle to stay ahead of the technology curve. The future is now and we must prepare for the impact of AI on our security environments.
Track 2
The Myth of Cybersecurity
Presented by Mike Crandall, CEO at Digital Beachhead
Cybersecurity is in the news with many high level breaches, however, many small to midsize businesses feel they cannot afford to implement any measures to protect themselves. The "Myth" of cybersecurity is that it is a destination instead of a journey. Instead, focus on Cyber Risk Management which provides a roadmap of doing what you can with what you have. It isn't about the latest"gadget" or technology but more about getting the most out of what you can afford andor currently have.
Modernizing the RMF to Combat Cyber Threats
Presented by Cherie Laliberte, Cybersecurity Engineer at Booz Allen Hamilton
The National Institute of Standards and Technology (NIST) developed RMF as a comprehensive, flexible risk-based framework. Instead of a compliance-based exercise, a modernized RMF approach provides holistic techniques to system security. Infusing cybersecurity, threat modeling, engineering principles, and software development together strengthens the overall security posture of systems. This approach provides solutions that present the overall risk posture and create innovative mitigations.
Cyber Assessment Mayhem
Presented by Ben Kreutzberg, Senior Cybersecurity Engineer at CyberNEX
The cyber world is riddled with assessments. Everywhere you look, an assessment is occurring. Do you need an assessment? Which assessment is right for your organization? Which assessments are required for your industry? Are you being assessed, and you don’t even know it? Let’s take a look at some of the common Cyber Assessments and break them down. We will discuss the goals and outcomes of common assessments to ensure you are getting, or performing, the desired assessment.
Risk, Situational Awareness and Information Systems
Presented by Aaron Shaha, CISO at Darklight, Inc.
How can we use the understanding of risk in our company and use our limited resources to defend ourselves effectively? What are some systemic problems in the industry and how can we help solve them? This will be specifically focused on risk and focus on small and medium business, but will be applicable to all.
Risk Perception on Cloud Adoption
Presented by Justin Jetton, Roswell Digital Insight
This session talks about the user acceptance on cloud technologies and how risk perception impacts the overall willingness to accept cloud technologies. Though the study focused on small and solo practitioner law firms the insights gained from the study impact executive and small business owners across industries.
Methods to measure Cybersecurity Posture and Effectiveness
Presented by Justin Jetton, Roswell Digital Insight
Going beyond key performance indicators, explore a better approach to measuring cyber defense postures.
Enhancing Blockchain Transactions with AI and Machine Learning
Presented by Barry Hess, COO at KnowledgeBridge International (KBI)
As blockchain technology continues to expand while the maturity of AI also continues to grow, how can we leverage these two technologies together to improve the security of our blockchain transactions and ultimately the security of networks into the next decade. This talk explores where we can take AI and machine learning to secure a networked future using the blockchain.
Workshops & CTFs
Hack Our Drone
Presented by Ronald Broberg, Dark Wolf Solutions
The Hack Our Drone Workshop provides participants with the opportunity to work through 'hands-on' lab modules focused on the components of an Unmanned Aerial System including the Vehicle (UAV), Ground Control System (GCS), and communication subsystem. Participants are expected to bring a laptop either with Kali Linux installed or bootable to a Kali Linux USB Thumb drive. All other equipment is provided.
Unmanned Aerial Systems – Platform Security CTF
Presented by CT Cubed
Discover the exciting world of cybersecurity and unmanned aerial systems (UAS)! Learn how to safeguard UAS from all angles with a comprehensive platform security perspective. Engage in some fun and challenging CTF adventures where you can put your skills to the test. See firsthand how your actions affect our UAS demonstrator. The UAS demonstrator contains all the sensors from our Mobile Optical Ultrasonic Sensor Explorer, or MOUSE for short. The MOUSE represents a small Unmanned Aircraft System (sUAS) comprising a pan/tilt object recognition camera, navigation camera, temperature & humidity sensor, ultrasonic sensor, and drive system powering four motors. You won't need to worry about any complicated registration process; all you need is your personal laptop to join in the excitement. Earn enough points in the challenge, and you could be the proud owner of a CT Cubed SAO, a special prize while supplies last. Get ready to embark on this fascinating journey and prove your cybersecurity prowess!
Wireless Capture the Flag (CTF)
Presented by Ronald Broberg, Dark Wolf Solutions
Wireless Capture the Flag offers both WiFi 802.11 challenges and other radio frequency challenges across the spectrum. Bring your own gear or borrow some of ours. Introductory walk-throughs will be offered to those who just want to come and learn.
BSides Colorado Springs CTF
Presented by Hackers N' Hops
A beginner to intermediate difficulty, jeaparody style CTF featuring a variety of challenge categories including OSINT, Crypto, and Root the Box.
Kid Track
Guardians of the Digital Realm
Get ready, young cyber detectives, for our 'Cyber Safety Adventure Workshop'! Join the mission to protect the digital world from cyber villains. Explore stations like 'Battle of the Bugs' and ' Malicious Worm Mania' to learn cybersecurity basics and become certified Cyber Safety Agents. Your mission: outsmart cyber villains and safeguard the digital realm!
Lunch Break
Sentinels of the Digital Frontier
Prepare yourselves, seasoned cyber sleuths, for our 'Advanced Cybersecurity Expedition'! Embark on a quest to defend the digital realm against cunning cyber adversaries. Engage in challenging activities to delve deeper into the world of cybersecurity. Your objective: outwit cyber adversaries and fortify the digital domain!
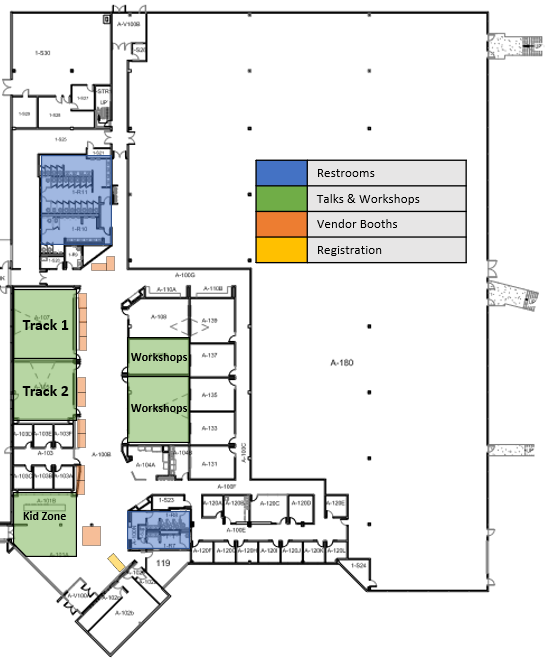
Day 1: Venue Map
Disclaimer: The conference schedule is subject to change without notice due to unforeseen circumstances. Attendees are advised to regularly check for updates on the official conference platform. We apologize for any inconvenience this may cause.